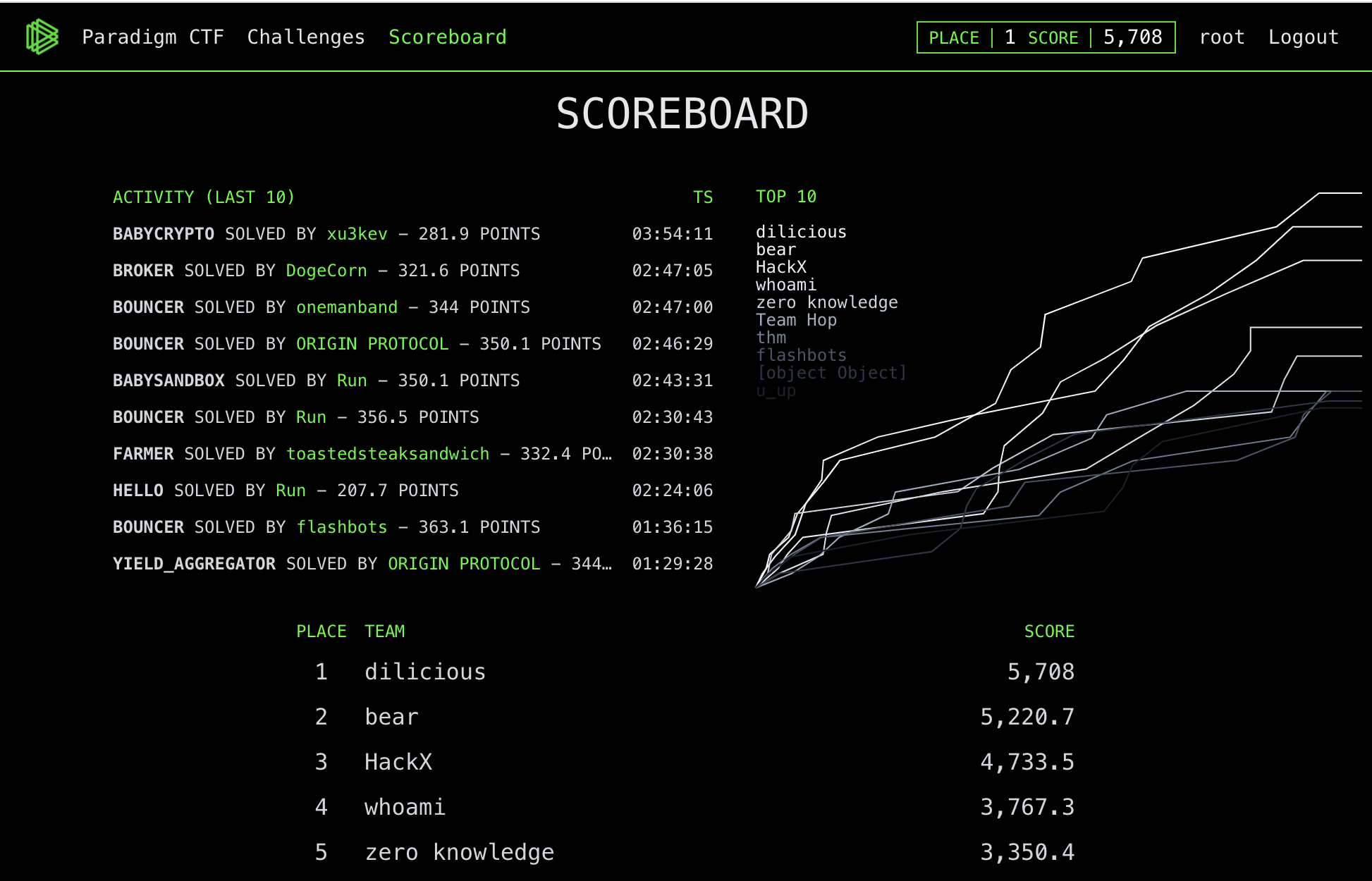
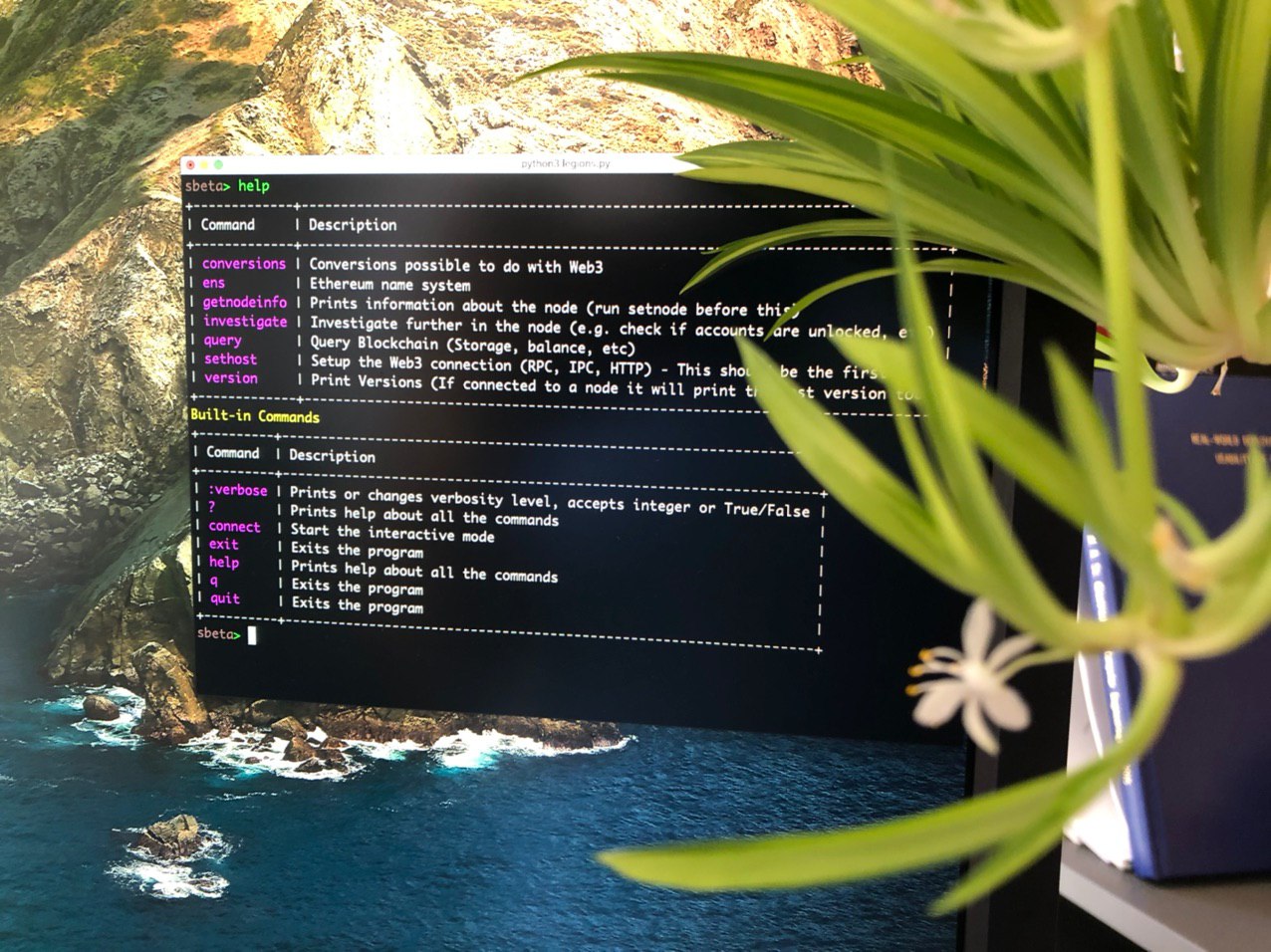
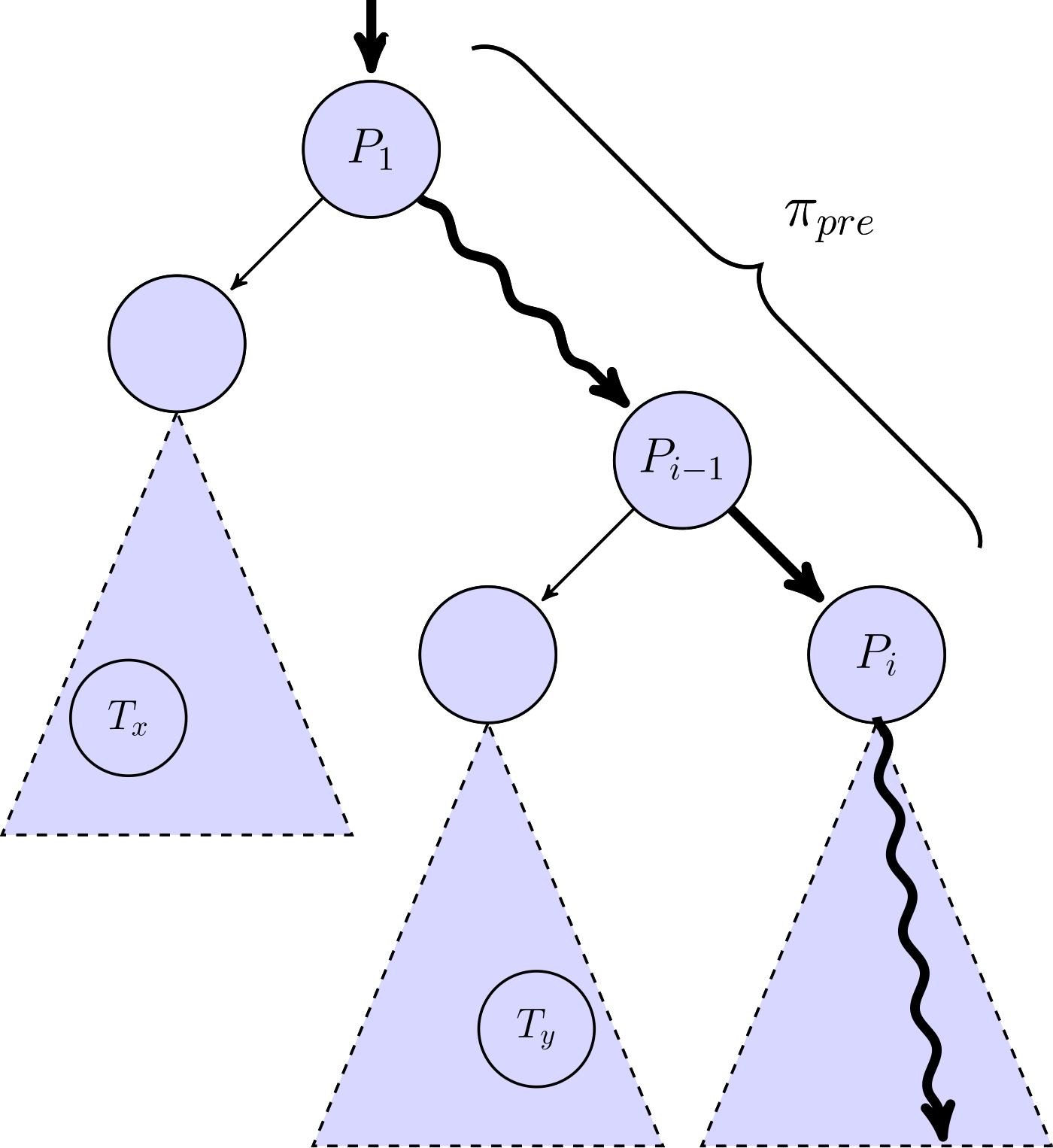
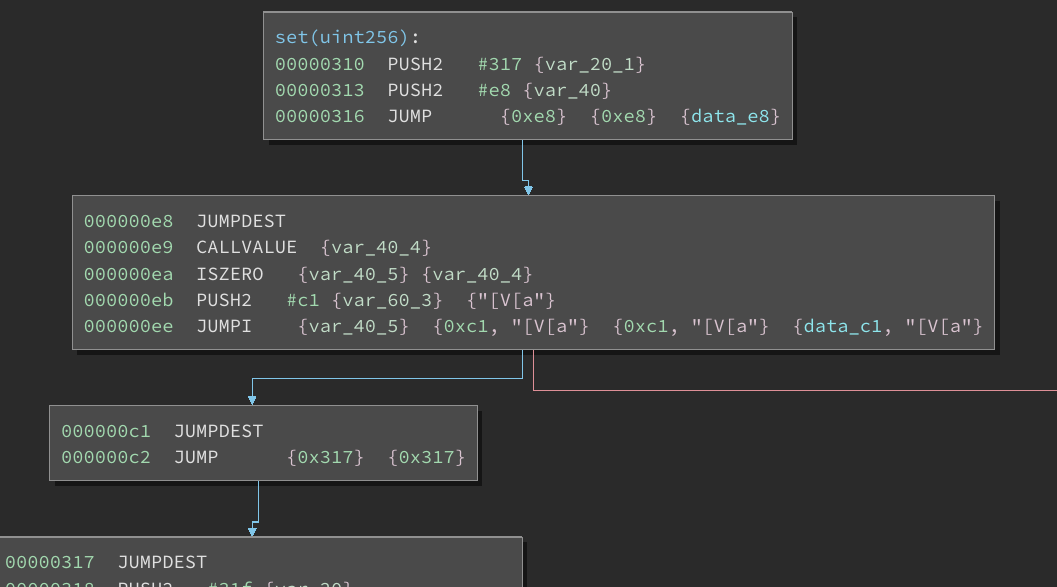
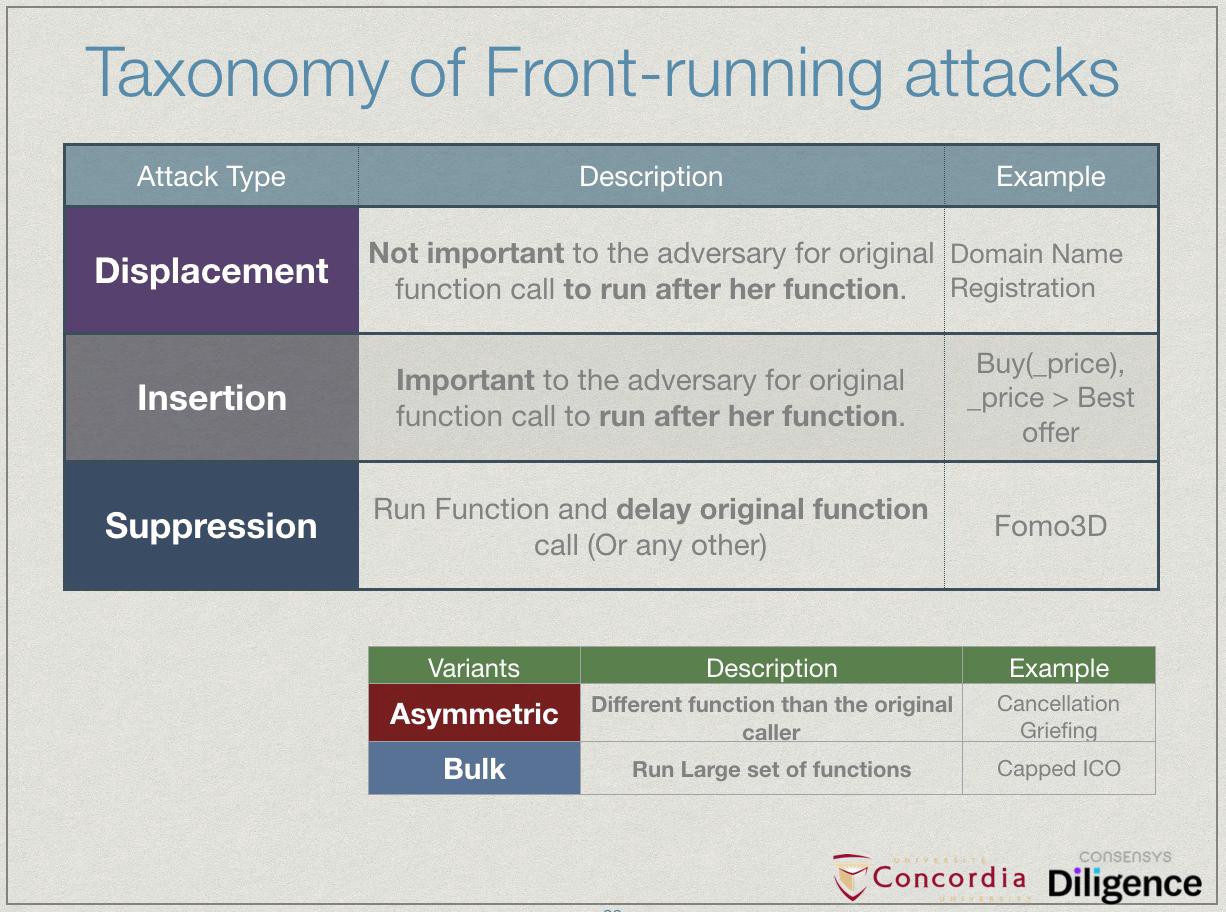
How Consensys Diligence Secures MetaMask Snaps and Linea
This blog highlights Diligences work across Consensys in auditing MetaMask Snaps and Linea components.
Tobias Vogel
May 23, 2024