As we learned earlier, blockchain bridges are necessary to facilitate communication and movement of assets between one network and another. This technology streamlines cross chain activity from L1 → L2, L2 → L2, L2 → L1, and even L1 → L1. In today’s tutorial, we take a look at trustless interoperability protocol Connext, which facilitates bridging and cross chain dApp deployment.
Why Connext?
Connext enables fast, non-custodial communication between chains and rollups. Their bridge protocol currently supports the transfer of funds between 17 networks. Unlike most other interoperability systems, Connext enables this without introducing any new trust assumptions or external validators, making the system more secure than architectures that use external validators.
They also suggest that “bridging is just the beginning of the story” in the next paradigm shift of Web3 interoperability, prompting them to launch an extensive toolkit not merely limited to bridges, but also cross chain dApp implementation. Builders can execute instructions from one central xApp (pronounced zap)—a decentralized app that performs operations between independent chains—instead of deploying on multiple chains.
For the purposes of this post, we’ll dive into the bridging component of their tech stack.
Sending Assets Using Connext
Ready to bridge your assets over? Head over to Connext’s bridging portal here.
Make sure to have your MetaMask wallet with the assets you’d like to transfer. And remember, you can always fund your wallet directly within MetaMask by hitting the blue “BUY” button in your home screen.
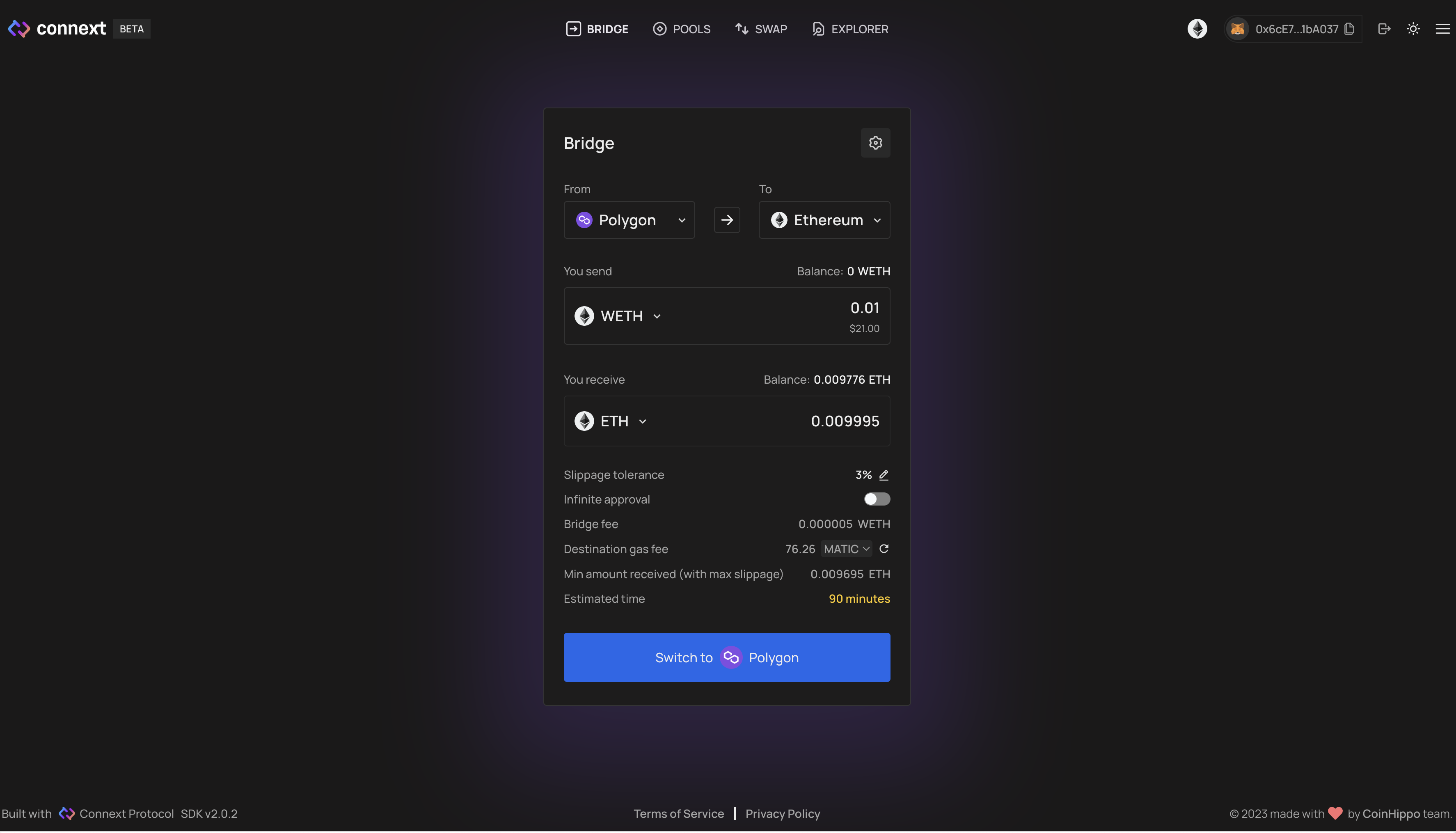
1. Connect your wallet in the top right corner and select MetaMask.
2. Once connected, choose what network you want to bridge TO and FROM in the dropdown menu. Example: Polygon to Ethereum Mainnet
3. After selecting your network and token you want to bridge, input the token amount in the box and select ‘Send’. Example: 0.01 WETH
4. Review the transfer and approve the transaction in your MetaMask wallet
5. Done! You will notice the network you bridged to funded with your tokens.
You can bridge from any of the 17 networks—you could bridge from Optimism to Arbitrum or Ethereum Mainnet, and even to alt L1 chains like BNB Chain—using Connext to transfer your assets.
How It Works
Connext’s infrastructure makes cross chain activity possible, whether it’s through bridging funds or enabling cross chain applications, referred to as xApps.
Connext is built with an hub-and-spoke model, which relies on Ethereum for security. This design allows messages to be passed between different chains by plugging directly into the native bridges of the various chains and L2s that connect an ecosystem to Ethereum.
For example, if a user wants to bridge from Optimism to Arbitrum, the Connext bridge will bridge tokens from Optimism to Ethereum through the Optimism native bridge, and then from Ethereum to Arbitrum through the Arbitrum canonical bridge, all in a seamless way.
Because the time required to move tokens through canonical bridges can be very long, Connext has a network of Routers that forward tokens to the user on the destination chain and then claim their funds back when eventually a slower batched transfer arrives on the destination chain via those canonical bridges.
This makes Connext the first Modular Interoperability Protocol that gives users and developers the best possible trust guarantees for whichever chains they want to bridge to.
The Connext protocol defines four core actors—(1) the user, (2) the Connext Router, (3) the messaging layer that relies on native bridges, and (4) the Watchers.
More actors are involved, though we can leave them aside for now.
Let’s take a look at the simplified process flow and how these actors work together:
The user (let’s call her Alice) sends a transaction to the Connext Smart Contract on the source chain signaling the Connext Routers that she wants to bridge.
A Connext Router—there are several—will see Alice’s transaction including the instructions. The Router will send the intended amount to Alice on the destination chain minus a fee. Now Alice is fine, but how does the Router get the money back?
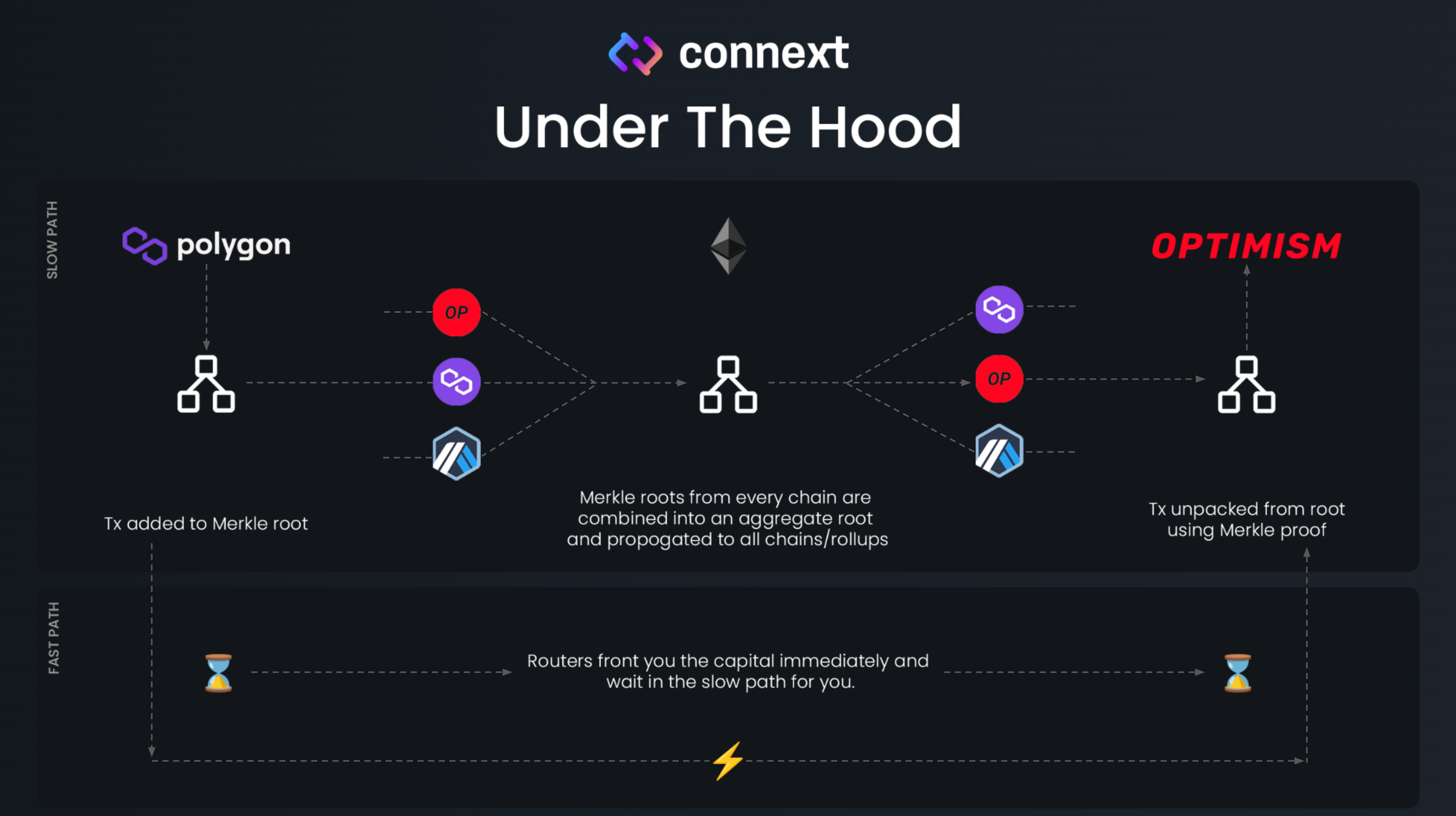
Under the hood and on the source chain, the Connext Smart Contract will forward Alice’s funds through the native bridge that connects a chain to Ethereum. The Connext Smart Contract on Ethereum aggregates several transactions together into an update in the form of a merkle tree.
The resulting root is then propagated back to the various chains so they all have an up-to-date overview of the balances. Now, the Connext Watchers have 30 minutes to step in if the update is fraudulent. The watcher can compare the balances of tokens locked on Ethereum versus the tokens available on the various spoke chains.
If nothing is fraudulent, then the Connext Router can claim its tokens back on the destination chain using the proof that it has already sent tokens to Alice in Step 2.
Connext Routers need to stake tokens ($NEXT) in order to participate in the network and earn a proportional share of work from the network in return.
“NEXT keeps the network running by ensuring that all routers are beholden to the same set of rules around fair transaction ordering, and a router’s NEXT is slashed if they violate these rules.” – What’s $NEXT?
Final Thoughts
Connext’s extensive list of networks is likely to keep growing and they allow you to bridge cheaply and rapidly without introducing any new trust assumptions. If you’re looking for a secure, trustless protocol to transfer your assets, consider Connext your next (🥁) protocol to try out.
Here’s a recap:
Go to bridge.connext.network
Connect your MetaMask wallet
Select the network you want to transfer TO and FROM
Select the asset you want to transfer
Click “Send” and sign the transactions in MetaMask to start the transfer
Voila!
While a lot of bridges have popped up in the space, the ones that have a heavy emphasis on security will prevail.
Enjoy connecting your way around Web3!
